
Distributed method for cracking WPA/WPA2‐PSK on multi‐core CPU and GPU architecture - Yong‐lei - 2015 - International Journal of Communication Systems - Wiley Online Library

How to use precomputed tables to crack Wi-Fi passwords in Hashcat and John the Ripper - Ethical hacking and penetration testing

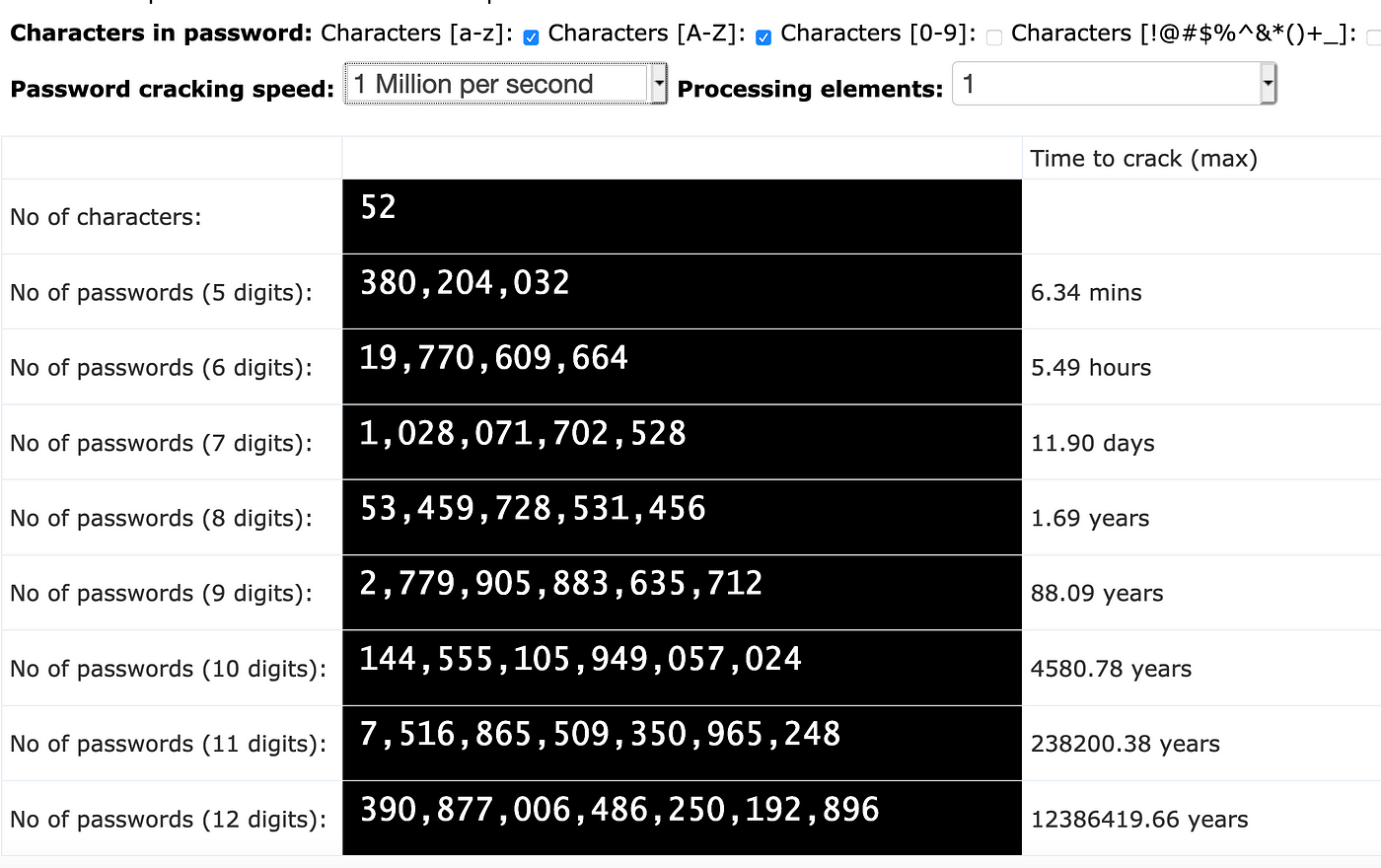
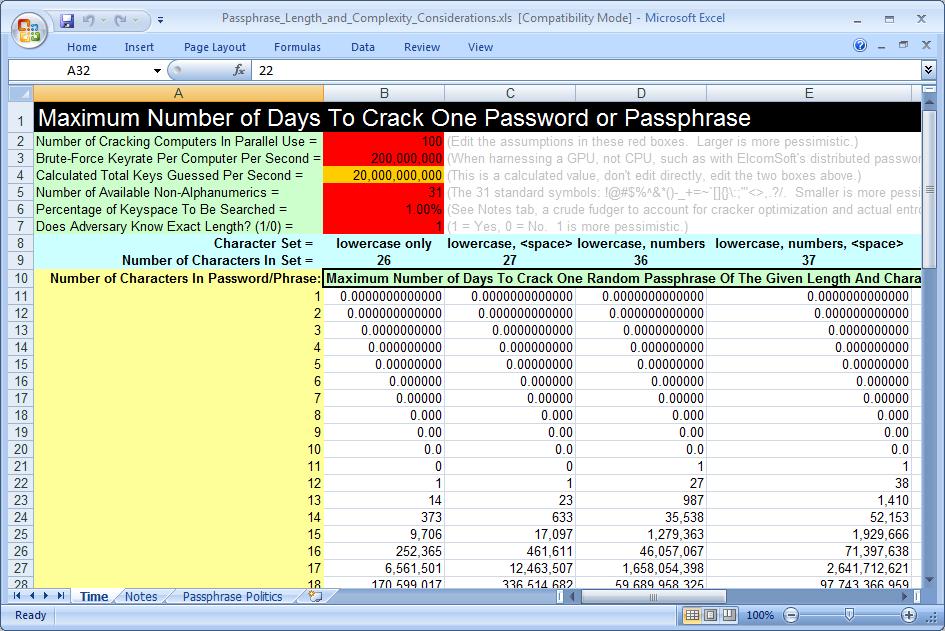
wifi - How long would it take to brute force an 11 character single-case alphanumeric password? - Information Security Stack Exchange
Electronics | Free Full-Text | A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3
The Problem With Passwords…. A couple of comments I received… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

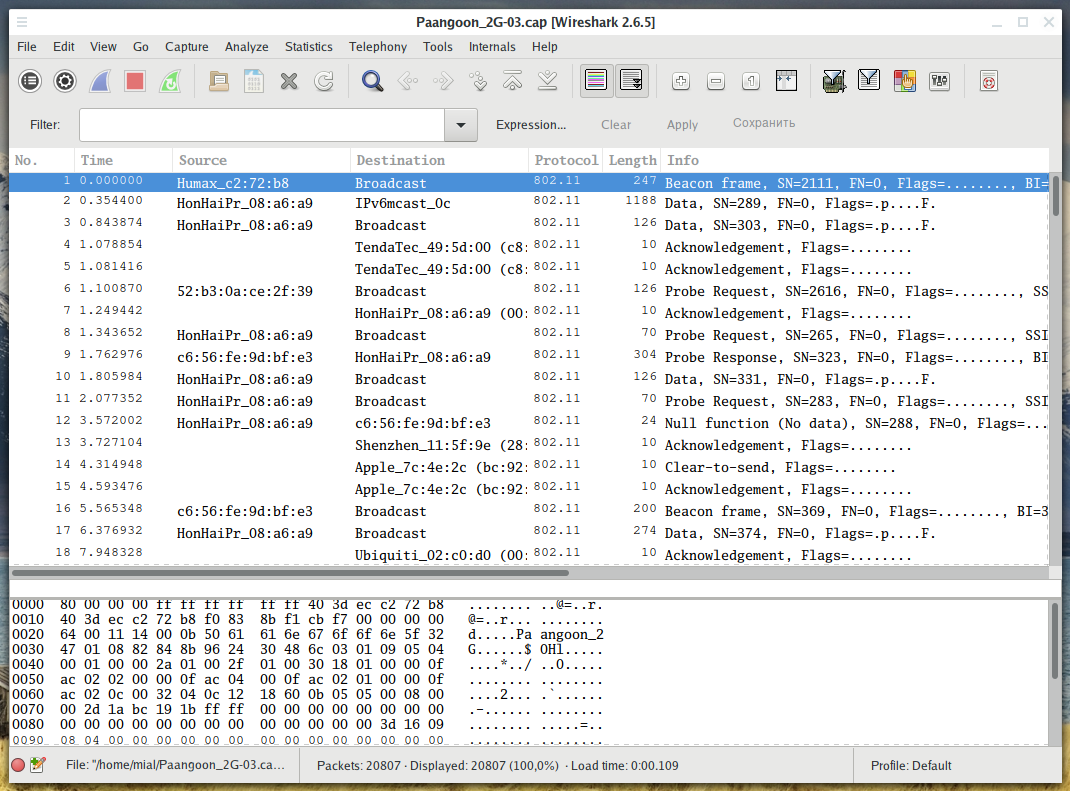
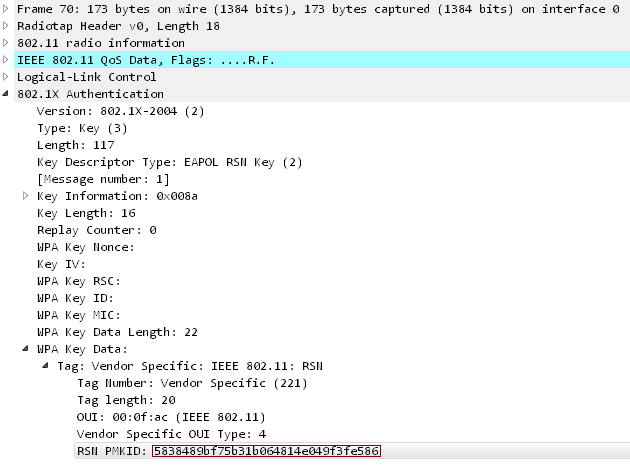
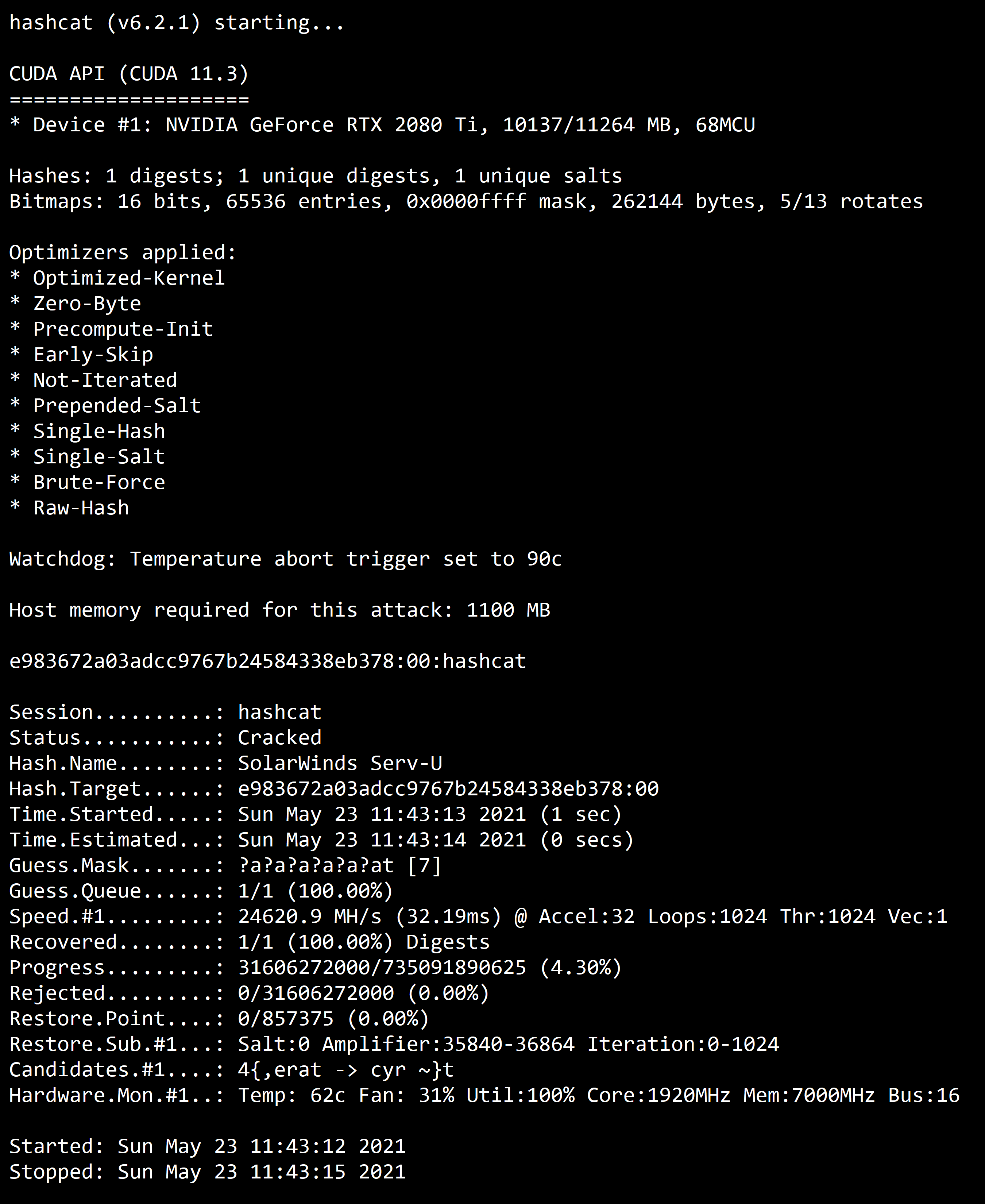

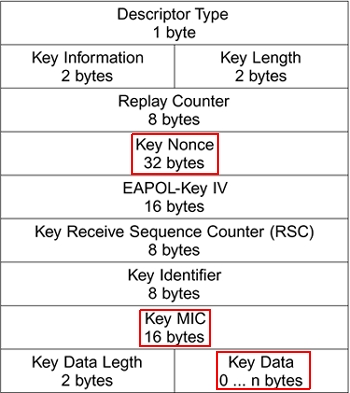
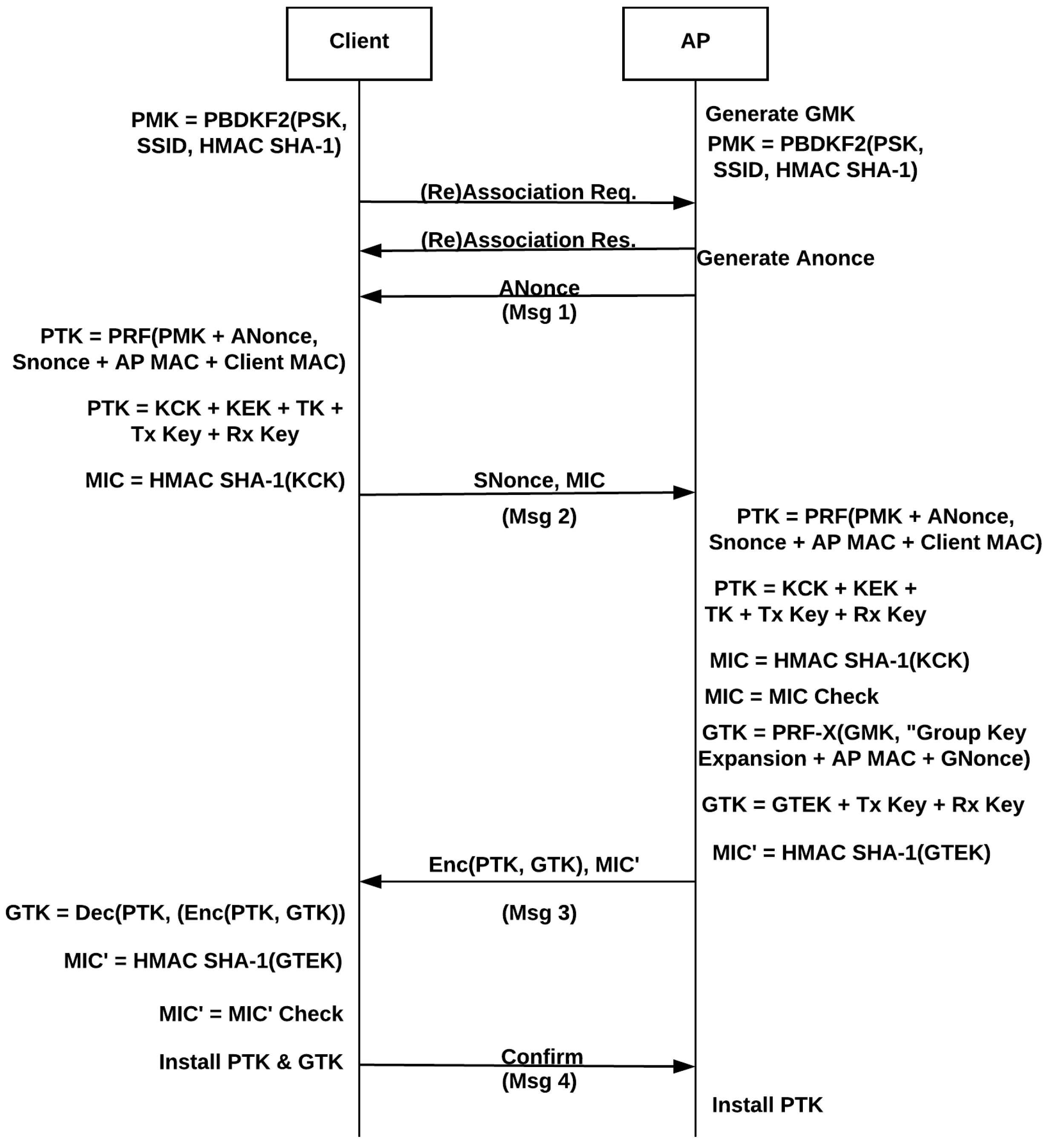
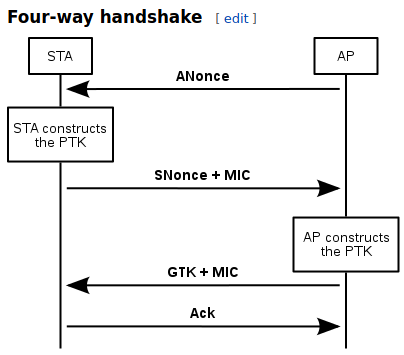
![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/wpa_wpa2_6_.jpg)
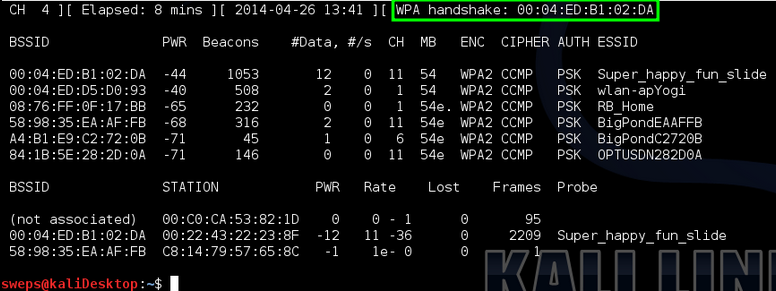
![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/Capturing_WPA_WPA2_Handshake_bg.jpg)

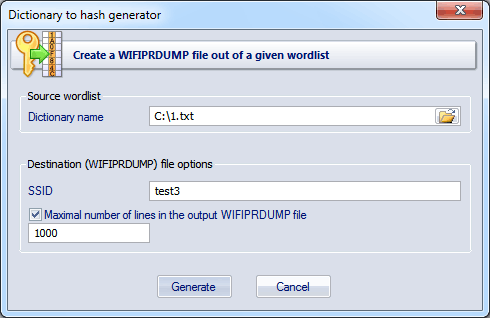
![WiFi Password Remover] Wireless (WEP/WPA/WPA2) Password/Profile Removal Software WiFi Password Remover] Wireless (WEP/WPA/WPA2) Password/Profile Removal Software](http://4.bp.blogspot.com/-qvyJrP3vZgo/UpDISY-bvSI/AAAAAAAABQA/sc7ZH95qnMQ/s1600/wifipasswordremover_mainscreen_big.jpg)
![Wi-Fi Password Key Generator] Wireless WEP/WPA/WPA2 Security Key Maker Tool Wi-Fi Password Key Generator] Wireless WEP/WPA/WPA2 Security Key Maker Tool](http://1.bp.blogspot.com/-xlzK5dxY8vQ/UmwocqbG4JI/AAAAAAAABIU/dfpzrkgYog4/s640/wifipasswordkeygenerator_mainscreen_big.jpg)

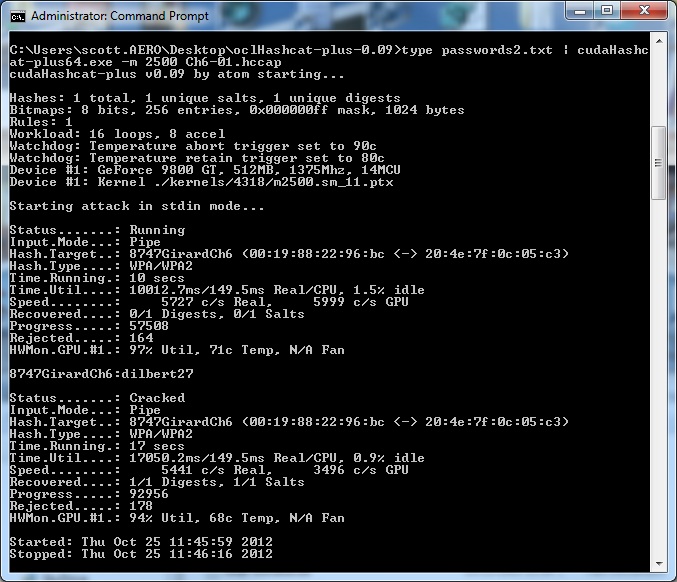
![oclHashcat-plus v0.14] Worlds fastest md5crypt, phpass, mscash2 and WPA/WPA2 cracker oclHashcat-plus v0.14] Worlds fastest md5crypt, phpass, mscash2 and WPA/WPA2 cracker](https://1.bp.blogspot.com/-yNn-_HQOgsA/UU0XZEp2MLI/AAAAAAAAAWU/QfF6sxmUqC0/s1600/oclhashcat-plus.png)